Palo Alto PA-5250 Hardware Appliance (End of Sale/Life)
PA-5250 Hardware Firewall
Product information "Palo Alto PA-5250 Hardware Appliance (End of Sale/Life)"
Limited budget? - Request your attractive offer now
Please note that an order outside the DACH region must be authorised by the manufacturer and processing can therefore not be guaranteed.
Please note that a license is mandatory for the operation of the hardware.
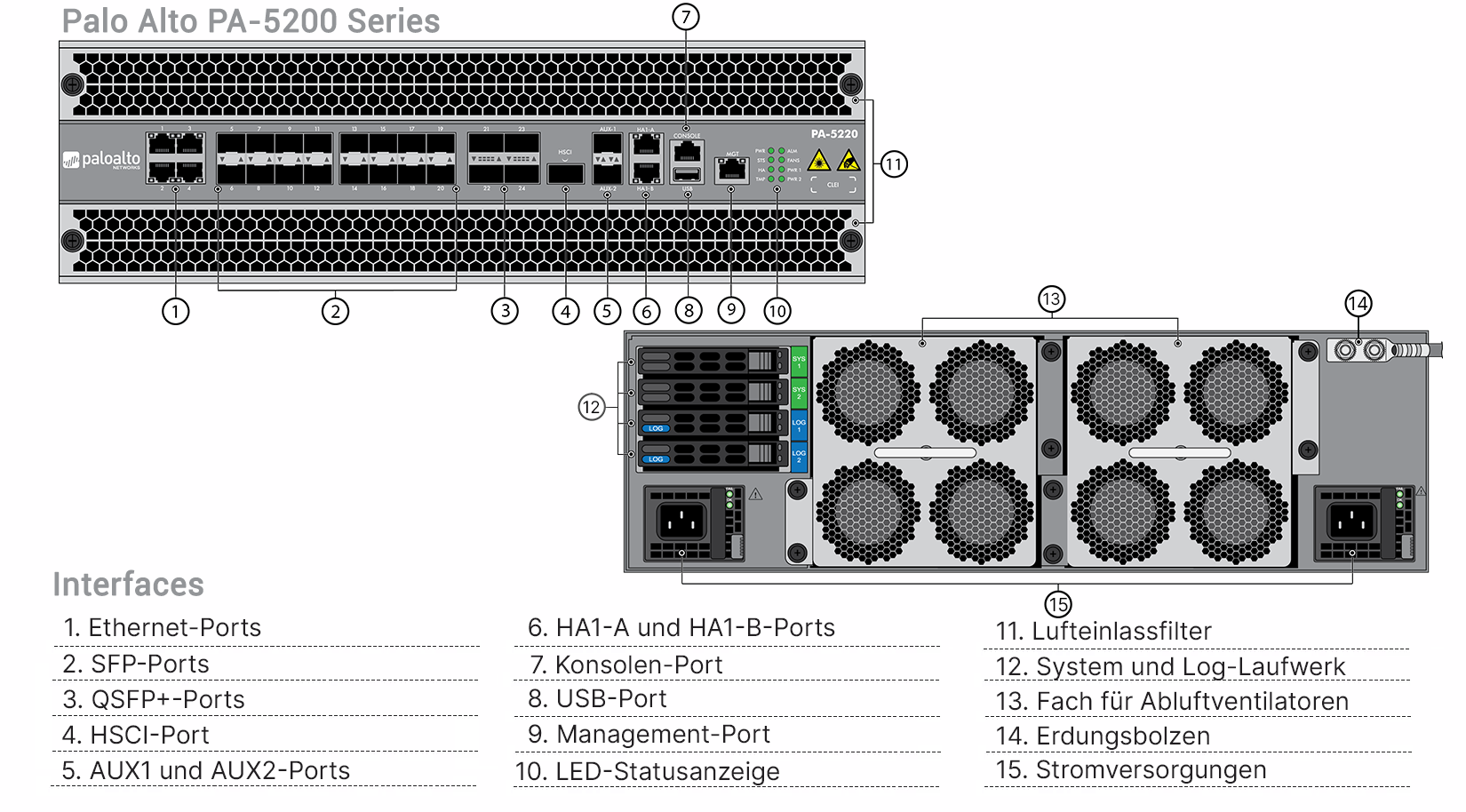
Palo Alto Networks PA-5200 Series ML-Powered NGFWs—the PA-5280, PA-5260, PA-5250, and PA-5220—are ideal for high-speed data center, internet gateway, and service provider deployments. The PA-5200 Series delivers up to 64 Gbps of throughput, using dedicated processing and memory, for the key functional areas of networking, security, threat prevention, and management.
Highlights:
- World’s first ML-Powered NGFW
- Eleven-time Leader in the Gartner Magic Quadrant for Network Firewalls
- Leader in The Forrester Wave: Enterprise Firewalls, Q4 2022
- Delivers 5G-Native Security built to safeguard service provider and enterprise 5G transformation and multi-access edge computing (MEC)
- Extends visibility and security to all devices, including unmanaged IoT devices, without the need to deploy additional sensors
- Supports high availability with active/active and active/passive modes
- Delivers predictable performance with security services
- Supports centralized administration with Panorama network security management
- Maximizes security investments and prevents business disruptions with Strata ™ Cloud Manager
The world’s first ML-Powered Next-Generation Firewall (NGFW) enables you to prevent unknown threats, see and secure everything—including the internet of things (IoT)—and reduce errors with automatic policy recommendations. The controlling element of the PA-5200 Series is PAN-OS ® , the same software that runs all Palo Alto Networks NGFWs. PAN-OS natively classifies all traffic, inclusive of applications, threats, and content, and then ties that traffic to the user regardless of location or device type. The application, content, and user—in other words, the elements that run your business— then serve as the basis of your security policies, resulting in improved security posture and reduced incident response time.
Palo Alto Lizenzmodell
* Inactive elements are not included in this bundle.
Detailed Palo Alto license information Palo Alto License Overview Palo Alto Functions
The most important security and connectivity features
ML-based next generation firewall
- Integrates machine learning (ML) into the core of the firewall to prevent signatureless inline file-based attacks and detect and immediately stop unprecedented phishing attempts.
- Uses cloud-based ML processes to send delay-free signatures and instructions back to the NGFW.
- Uses behavioral analytics to discover Internet of Things (IoT) devices and make policy recommendations; cloud-provisioned and natively integrated service on NGFW.
- Automates policy recommendations to save time and reduce the risk of operator error.
Identification and classification of all applications - at any time and with full Layer 7 verification.
- Identifies the applications that send data through your network, regardless of port, protocol, bypass techniques, or encryption (TLS/SSL).
- Allows defining and implementing security policies related to specific applications (instead of ports) (allow, deny, schedule, inspect, apply traffic rules).
- Provides the ability to create custom App-ID™ identifiers for your own applications or request App-ID development for new applications from Palo Alto Networks.
- Identifies all payloads within the application (such as files and data patterns) to block malicious files and prevent data leakage.
- Creates standard and customized application usage reports, including Software-as-aService (SaaS) reports that provide visibility into all approved and unapproved SaaS traffic on your network.
- Enables secure migration of legacy Layer 4 rule sets to App-ID-based rules with built-in Policy Optimizer. This gives you a rule set that is more secure and easier to manage.
Enforce security measures and adjust policies based on user activity
- Enables visibility, security policies, reporting and forensics based on users and groups - not just IP addresses.
- Integrates easily with a variety of repositories to leverage user information: WLAN controllers, VPNs, directory servers, SIEMs, proxies and more.
- Allows you to define dynamic user groups in the firewall to implement time-bound security measures without having to wait for user directories to update.
- Applies consistent policies regardless of users' locations (office, home, on the road, etc.) and their devices (iOS and Android® mobile devices; macOS®, Windows®, Linux desktops, laptops; Citrix and Microsoft VDI and terminal servers).
- Prevents corporate credentials from entering third-party sites and prevents the use of stolen credentials by enabling multi-factor authentication (MFA) at the network layer for each application without requiring the application to be modified.
- Based on user behavior, security measures are dynamically implemented to block suspicious or malicious users.
Protection against malicious activity hiding in encrypted traffic
- Inspects and applies policy to inbound and outbound TLS/SSL-encrypted traffic, including traffic that uses TLS 1.3 and HTTP/2.
- Provides comprehensive insights into TLS traffic, such as the amount of traffic encrypted, TLS/SSL versions, ciphersuites, and more, without decrypting it.
- Enables preventing the use of outdated TLS protocols, insecure ciphersuites, and misconfigured certificates to minimize risks.
- Facilitates decryption deployment and enables the use of built-in logs for troubleshooting, such as certificate pinning applications.
- Enables flexible enabling or disabling of decryption based on URL category and source and destination zone, address, user, user group, device, and port to maintain data privacy and regulatory compliance.
- Allows a copy of decrypted traffic to be made by the firewall (i.e., decryption mirroring) and sent to traffic capture tools for forensics, history logging, or data loss prevention (DLP).
Centralized management and transparency
- Leverages centralized management, configuration, and visibility for multiple Palo Alto Networks distributed NGFWs (regardless of location or scale) through Panorama™ network security management at a unified user interface.
- Simplifies configuration sharing via Panorama with templates and device groups, and scales log collection as needed.
- Provides users with detailed visibility and comprehensive insight into network traffic and threats through the Application Command Center (ACC).
Detect and defend against complex threats with cloud-delivered security services
Modern sophisticated cyberattacks can grow up to 45,000 variants within 30 minutes. Multiple threat vectors and sophisticated techniques are used to inject malicious code. Traditional point solutions create enterprise security gaps, increase the workload of security teams, and impact productivity through inconsistent access and poor visibility.
Palo Alto's cloud-delivered security services, on the other hand, seamlessly integrate with their industry-leading NGFWs and leverage Palo Alto's network of 80,000 customers to instantly coordinate threat intelligence and provide protection against all threats and threat vectors. Close security gaps across all your sites and take advantage of best-in-class security consistently delivered through a centralized platform to protect against even the most complex and well-disguised threats. These services are provided:
- Threat Prevention – provides more security than a traditional IPS (Intrusion Prevention System) by blocking all known threats to all traffic in one pass (single pass) without sacrificing performance.
- Advanced URL Filtering – delivers best-in-class protection against web-based threats and increased operational efficiency with the industry's first real-time web attack prevention solution and industry-leading phishing defense.
- WildFire® – protects files by automatically detecting and defending against unknown malware with industry-leading cloud-based analytics and threat intelligence from more than 42,000 customers.
- Advanced DNS Security – uses ML to detect and defend against threats in real time over the DNS. This gives security teams the contextual information they need to formulate policies and defend against threats quickly and effectively.
- IoT Security – provides the industry's most comprehensive IoT security solution for detailed visibility, effective defense, and robust policy enforcement - all on a single ML-powered platform.
- Enterprise DLP – provides the industry's first cloud-based enterprise DLP solution that consistently protects sensitive data across all networks, clouds, and users.
- SaaS Security – provides integrated SaaS security capabilities that help you discover and secure new SaaS applications, protect data, and defend against zero-day threats - all at the lowest total cost of ownership.
Unique approach to packet processing with single-pass architecture
- Performs network functions, policy search, application and decoding, and signature matching for all threats and content in a single pass. This significantly reduces the processing overhead of performing multiple functions in a single security system.
- Avoids latency by verifying traffic against all signatures in a single pass with stream-based, unified signature matching.
- Enables consistent and predictable performance when Security Subscriptions are enabled. (Threat prevention throughput in Table 1 is based on multiple enabled subscriptions).
SD-WAN functionality
- Enables you to deploy SD-WAN by simply enabling it on your existing firewalls.
- Enables you to securely deploy SD-WAN, natively integrated with our industry-leading security.
- Provides a premium user experience by minimizing latency, jitter, and packet loss.
Palo Alto PA-5250 Hardware Appliance (End of Sale/Life) Product information
| Bundle: | only Hardware |
|---|---|
| Firewalldurchsatz (HTTP/Appmix): | 38 Gbps / 37 Gbps |
| IPsec VPN Throughput : | 19 Gbps |
| Max. Sitzungen: | 8 Millionen |
| Neue Sitzungen pro Sekunde: | 382.000 |
| Threat Prevention-Durchsatz (HTTP/Appmix): | 19,5 Gbps / 24 Gbps |
| Term: | only Hardware |
only €111,505.17*
| Gross price: | €132,691.15 |
| Product number: | PAN-PA-5250-AC |
- No longer available
Please select your desired variant by clicking on the button below to display the respective product information.